Ossim 中漏洞扫描详解
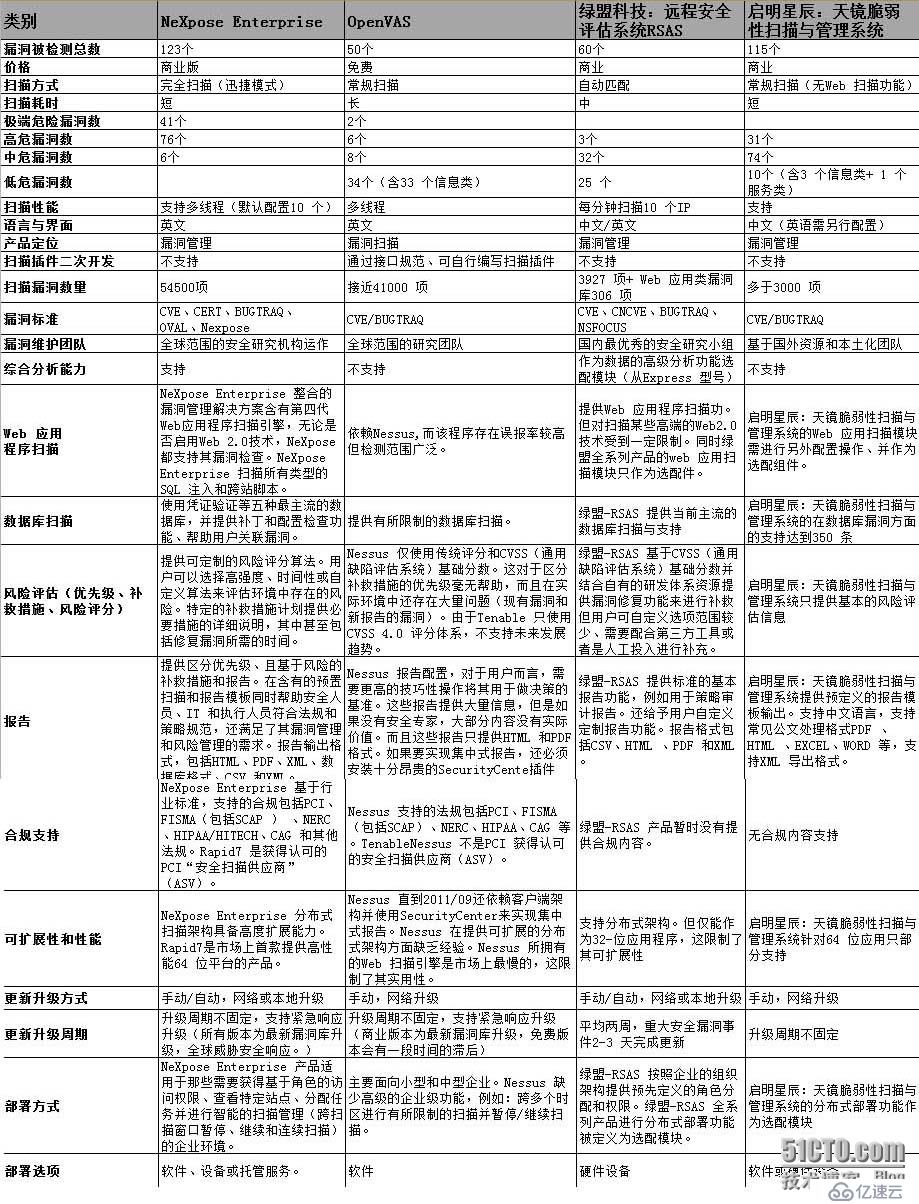
Openvas是一套开源漏洞扫描系统,如果手动搭建需要复杂的过程,花费不少人力和时间成本,因为它是套免费的漏洞扫描系统,功能上不逊色于商业版的漏洞扫描器,受到不少用户的青睐,下表对比了NeXpose、RSAS和启明的漏洞扫描器的主要功能。
有了以上背景之后,下文主要针对OSSIM平台下如何以图形化方式操作漏洞扫描的过程。
准备工作:首先确保没有运行的扫描进程和任务
扫描漏洞同时升级漏洞库会导致升级失败。
第一步:同步插件
#openvas-nvt-sync
[i] This script synchronizes an NVT collection with the 'OpenVAS NVT Feed'.
[i] The 'OpenVAS NVT Feed' is provided by 'The OpenVAS Project'.
[i] Online information about this feed: 'http://www.openvas.org/openvas-nvt-feed.html'.
[i] NVT dir: /var/lib/openvas/plugins
[i] Will use rsync
[i] Using rsync: /usr/bin/rsync
[i] Configured NVT rsync feed: rsync://feed.openvas.org:/nvt-feed
OpenVAS feed server -
This service is hosted by Intevation GmbH -
All transactions are logged.
Please report synchronization problems to openvas-feed@intevation.de.
If you have any other questions, please use the OpenVAS mailing lists
or the OpenVAS IRC chat. See for details.
receiving incremental file list
deleting gb_openssl_38562.nasl.asc
deleting gb_openssl_38562.nasl
./
COPYING
588 100% 574.22kB/s 0:00:00 (xfer#1, to-check=13347/13355)
COPYING.GPLv2
18002 100% 17.17MB/s 0:00:00 (xfer#2, to-check=13346/13355)
COPYING.files
1819904 100% 1.77MB/s 0:00:00 (xfer#3, to-check=13345/13355)
DDI_Directory_Scanner.nasl
32957 100% 32.74kB/s 0:00:00 (xfer#4, to-check=13342/13355)
DDI_Directory_Scanner.nasl.asc
198 100% 0.20kB/s 0:00:00 (xfer#5, to-check=13341/13355)
... ...
同步数万个插件时间比较长,消耗资源不大,可以去喝杯咖啡啦,或者了解一下插件的组成。
表1 Openvas主要脚本分类及分布情况
规则名称
数量
备注
IIS_frontpage_DOS_2.nasl
1
phpbb
8
RA_ssh_detect
RA_www_css
RA_www_detect
3
RHSA_2009_03**
279
Redhat Security Advisory
3com_switches
1
weblogic*
3
cisco_ids
cisco_***
ciscoworks
16
awstats
4
apache
23
DDI
30
EZ_hotscripts
3
anti_nessus
1
basilix
8
bluecoat
1
bugbear
3
bugzilla
9
ca_unicenter
2
cacti
5
calendar
3
Spoll_7_5_sql_injection
2
avaya_switches
1
citrix
8
clamav
2
CUPS
12
cutenews
12
checkpoint
6
cheopsNG
4
cvstrac
24
DB2
4
deb_*.nasl
2595
Debian Linux
5
deluxeBB
3
eftp
3
ls exchange*
exchange
2
fcore
684
find_service
5
fortigate
1
freebsd
2009
ftp
30
gb_CESA
1528
gb_RHSA
871
gb_adobe
167
gb_apple
70
gb_baofeng_storm
3
gb_bpsoft
3
gb_clamav
16
gb_ccproxy
2
gb_clamav
16
gb_fedora
4679
gb_google
162
gb_hp_ux
242
HP-UNIX
gb_ibm_db2
27
gb_ibm_websphere
8
gb_ibm_tivoli
5
gb_ibm_was
16
gb_ibm_lotus
10
gb_mandriva
1684
gb_java
2
gb_kaspersky
6
gb_google_chrome
153
gb_foxmail
2
gb_fsecure
7
gb_ms
155
Windows 相关
gb_ubuntu
1261
gb_samba
12
gb_sun_java
35
gb_wireshark
87
glsa
1727
gb_vmware
41
IIS
20
lotus
5
ipswitch
5
5
gb_nmap
187
nortel
7
nagios
5
openssh
4
oscommerce
5
postgresql
5
phpgroupware
12
phpmyadmin
7
phpbb
8
smb
52
sendmail
15
suse
65
ssh
11
smtp
9
Ubuntu
179
tomcat
6
tftp
11
wu_ftpd
6
第二步:更新插件(做这一步操作,建议在轻负载下进行)
#perl /usr/share/ossim/scripts/vulnmeter/updateplugins.pl migrate /* 比较消耗CPU和磁盘I/O */
2015-09-07 07:27:33 Framework profile has been found...
2015-09-07 07:27:33 Deleting all tasks in 192.168.11.150 ...
2015-09-07 07:27:33 updateplugins: configured to not updateplugins
2015-09-07 07:27:33 updateplugins: configured to not repair DB
2015-09-07 07:27:33 BEGIN - DUMP PLUGINS
2015-09-07 07:29:01 FINISH - DUMP PLUGINS [ Process took 88 seconds ]
2015-09-07 07:29:01 BEGIN - IMPORT PLUGINS
2015-09-07 07:30:00 FINISH - IMPORT PLUGINS [ 40473 plugins - Process took 59 seconds ]
2015-09-07 07:30:00 BEGIN - UPDATE CATEGORIES
2015-09-07 07:30:00 FINISH - UPDATE CATEGORIES [ Process took 0 seconds ]
2015-09-07 07:30:00 BEGIN - UPDATE FAMILIES
2015-09-07 07:30:00 FINISH - UPDATE FAMILIES [ Process took 0 seconds ]
2015-09-07 07:30:00 BEGIN - UPDATE OPENVAS_PLUGINS
2015-09-07 07:30:03 FINISH - UPDATE OPENVAS_PLUGINS [ Process took 3 seconds ]
2015-09-07 07:30:03 BEGIN - UPDATE NESSUS_PREFERENCES
2015-09-07 07:30:03 show tables like "vuln_nessus_preferences_defaults"
2015-09-07 07:30:03 updateprefs: Getting plugin preferences
2015-09-07 07:30:05 FINISH - UPDATE NESSUS_PREFERENCES [ Process took 2 seconds ]
2015-09-07 07:30:06 Creating Deep profile...
2015-09-07 07:30:06 Filling categories...............
2015-09-07 07:30:06 Done
2015-09-07 07:30:06 Filling families.............................................................
2015-09-07 07:30:06 Done
2015-09-07 07:30:06 Filling plugins...
2015-09-07 07:30:13 Filling preferences in Alienvault DB...
2015-09-07 07:30:14 Done
2015-09-07 07:30:14 Deep profile inserted
2015-09-07 07:30:15 Creating Default profile...
2015-09-07 07:30:15 Filling categories...............
2015-09-07 07:30:15 Done
2015-09-07 07:30:15 Filling families.............................................................
2015-09-07 07:30:15 Done
2015-09-07 07:30:15 Filling plugins...
2015-09-07 07:30:23 Filling preferences in Alienvault DB...
2015-09-07 07:30:24 Done
2015-09-07 07:30:24 Default profile inserted
2015-09-07 07:30:24 Creating Ultimate profile...
2015-09-07 07:30:24 Filling categories...............
2015-09-07 07:30:24 Done
2015-09-07 07:30:24 Filling families.............................................................
2015-09-07 07:30:24 Done
2015-09-07 07:30:24 Filling plugins...
2015-09-07 07:30:32 Filling preferences in Alienvault DB...
2015-09-07 07:30:33 Done
2015-09-07 07:30:33 Ultimate profile inserted
2015-09-07 07:30:33 BEGIN - UPDATE PORT SCANNER
2015-09-07 07:30:35 FINISH - UPDATE PORT SCANNER [ Process took 2 seconds ]
Updating plugin_sid vulnerabilities scanner ids
plugins fetched
Updating...
Script id:94151, Name:IT-Grundschutz M4.288: Sichere Administration von VoIP-Endger?ten, Priority:0
Script id:703073, Name:Debian Security Advisory DSA 3073-1 (libgcrypt11 - security update), Priority:1
Script id:804624, Name:Adobe Reader Plugin Signature Bypass Vulnerability (Windows), Priority:2
Script id:868149, Name:Fedora Update for kernel FEDORA-2014-9959, Priority:5
Script id:95048, Name:IT-Grundschutz M5.145: Sicherer Einsatz von CUPS, Priority:0
Script id:842216, Name:Ubuntu Update for linux USN-2616-1, Priority:4
Script id:105036, Name:Open××× Detection, Priority:0
Script id:868005, Name:Fedora Update for audacious-plugins FEDORA-2014-8183, Priority:1
Script id:869350, Name:Fedora Update for springframework FEDORA-2015-6862, Priority:5
… …
Script id:105084, Name:Multiple ManageEngine Products Arbitrary File Upload Vulnerability, Priority:3
Script id:867751, Name:Fedora Update for python-keystoneclient FEDORA-2014-5555, Priority:3
Script id:882209, Name:CentOS Update for nss CESA-2015:1185 centos6, Priority:2
Script id:842209, Name:Ubuntu Update for libmodule-signature-perl USN-2607-1, Priority:5
经过一刻钟等待终于更新完成。注意,该过程需要一气呵成,中途不能强制退出。
下面用时间轴表示每个步骤的演进顺序和所花费的时间,如下图所示。从某日的00:34:34开始到00:38:50结束的过程。
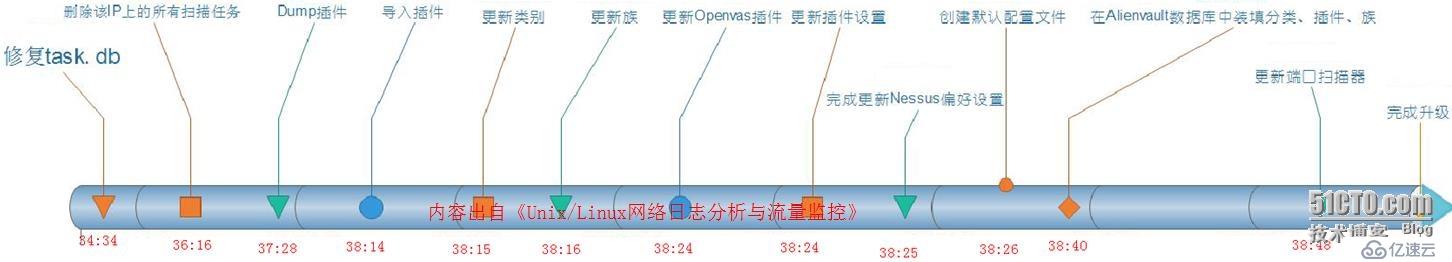
如果有些用户不习惯在CLI下操作升级命令,这一工作同样可以在WebUI中完成。
郑重声明:本文版权归原作者所有,转载文章仅为传播更多信息之目的,如作者信息标记有误,请第一时间联系我们修改或删除,多谢。
